New Security Measures from Gmail (VIDEO)
Have you noticed some of the changes lately in your Gmail inbox? You may have received an email from a friend or colleague and saw that it had an unlocked red padlock next to it like this: When you hover over the padlock,
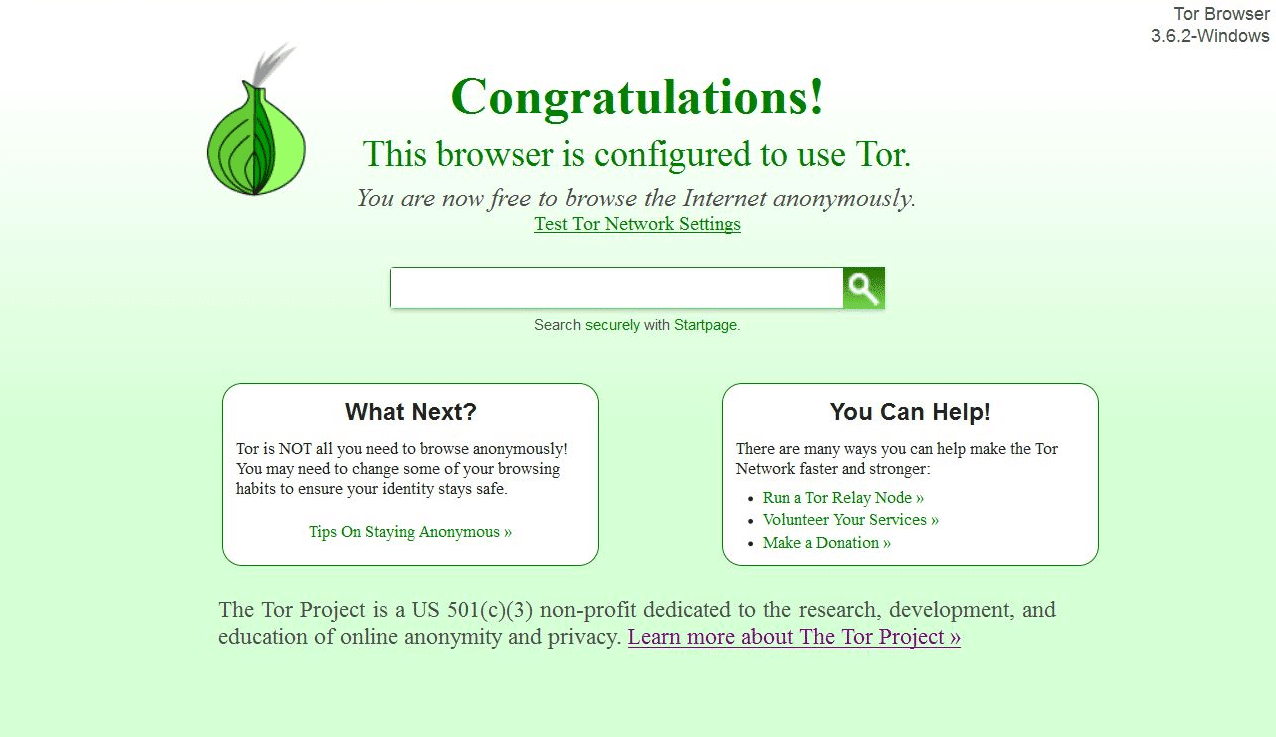
How to Install Tor Browser on Windows
One of the great things about the internet used to be the anonymity of it. You have the freedom to share information without compromising your privacy. However, with technology becoming ever better, it is becoming increasingly difficult to stay hidden on the web. If
How Do SSL Certificates Work?
How do you exchange private data over the internet? Part of the answer lies with SSL certificates. Secure Socket Layer (SSL) certificates work by creating a private line of communication in which allows private data to be delivered. The main problem with communication








Recent Comments